It’s no secret that ransomware has shaped conversations in the SOC this year more than any other topic, as attackers use new malware variants and other sophisticated techniques, tools and procedures to bypass conventional security tools. Not only are these attacks becoming more advanced and difficult to stop, but the ransom demands are growing, with one source suggesting the average ransom demand has grown by over 500% since last year.
To stop novel ransomware attacks, security teams need to turn away from ‘rear-view mirror’ tools trained on previous attacks, and towards AI technology that learns the business from the ground up and autonomously responds with targeted action to contain the threat.
This blog showcases how defenders can fight back against even the most sophisticated attacks, dissecting a recent ransomware attack uncovered by Darktrace’s AI from its first day of deployment at a utility services company. This was a particularly devastating ransomware strain known as Egregor, which has likely been disrupted by a joint effort between law enforcement agencies in Ukraine, France and the US, but wreaked havoc in the winter of 2020/21, affecting 150 companies and demanding ransoms of up to $4 million.
Anatomy of an Egregor attack

Figure 1: A timeline of the attack.
The initial intrusion occurred prior to Darktrace’s deployment, via Emotet, a trojan malware typically spread via spam emails – that has also been disrupted since this attack happened. Had Antigena Email been installed, Darktrace’s AI would have picked up on subtle deviations within malicious emails and actioned a response, containing the ransomware attack in its earliest stages. In this case, Antigena Email was not installed, and so the attack was allowed to proceed.
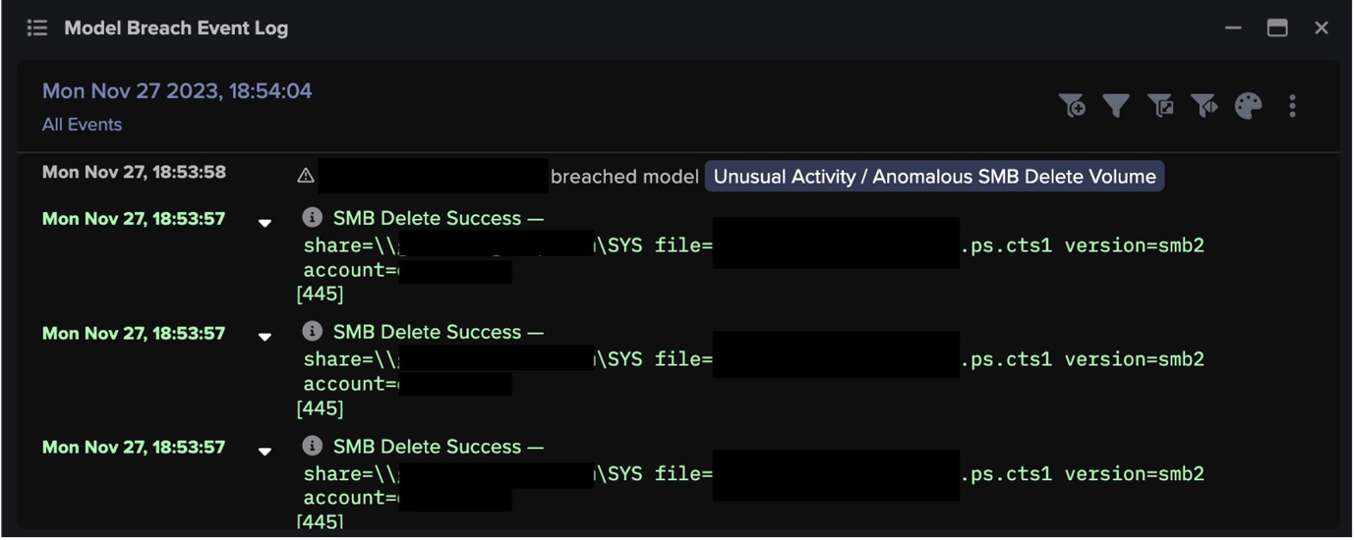
On November 27, 2020, Darktrace’s AI was deployed and began learning the ‘patterns of life’ for every user and device in the organization. On the first day of learning the organization, the technology detected suspicious external connections on a laptop that was deviating from the ‘pattern of life’ of its peer group of similar devices, beaconing to unusual rare domains that were later associated with malware activity.
A continuación, se observaron indicadores de movimiento lateral y escalada de privilegios, así como un posible intento de secuestro de correo electrónico. La IA de Darktrace detectó nuevas e inusuales solicitudes svcctl, nuevas llamadas a procedimientos remotos y escrituras sospechosas de archivos ejecutables a través de SMBv2, así como nuevas conexiones externas a través de puertos relacionados con el correo electrónico.
Connecting the dots: Cyber AI Analyst investigates
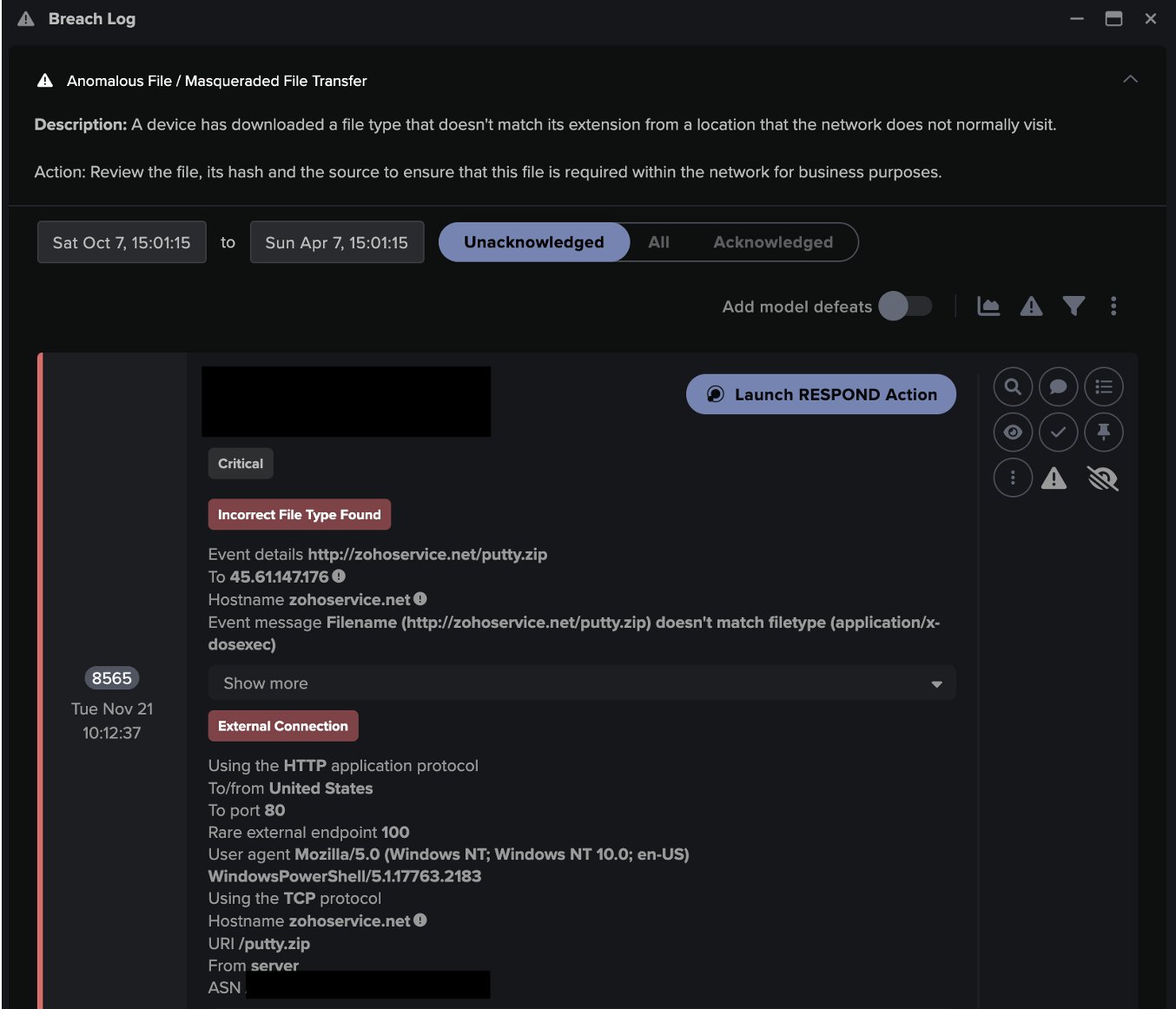
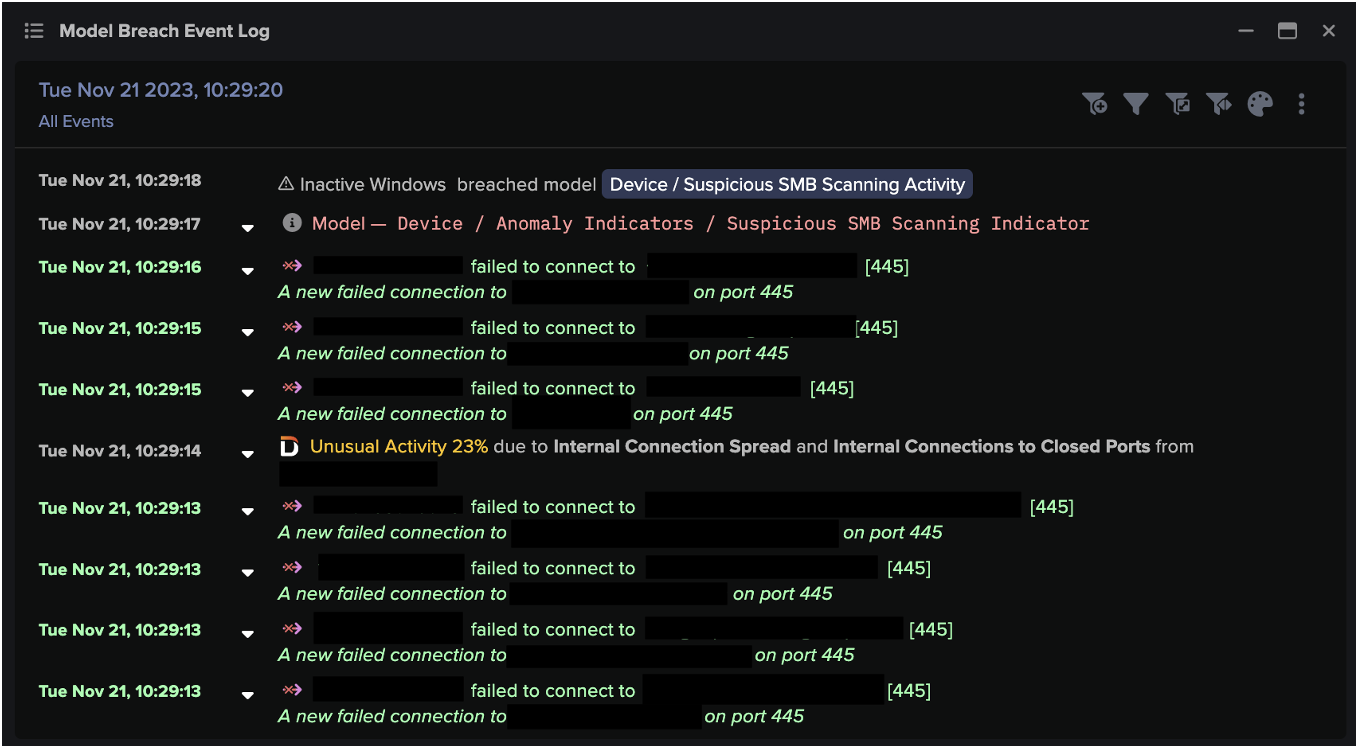
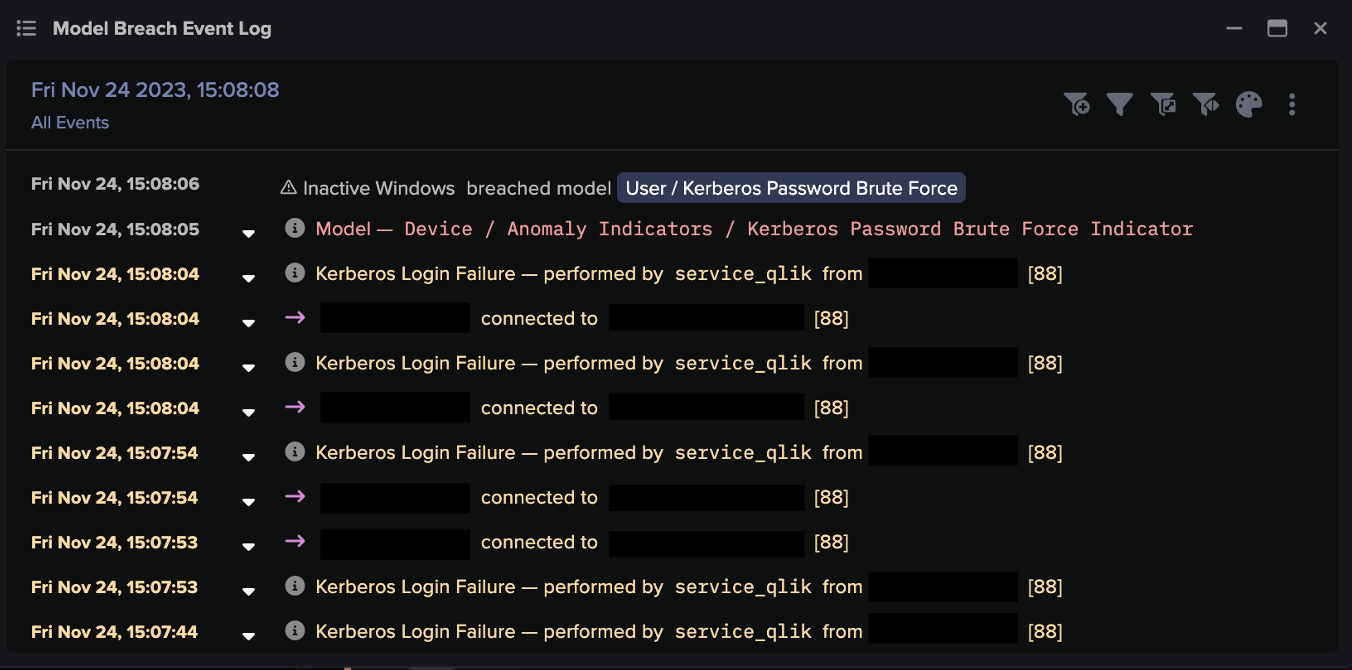
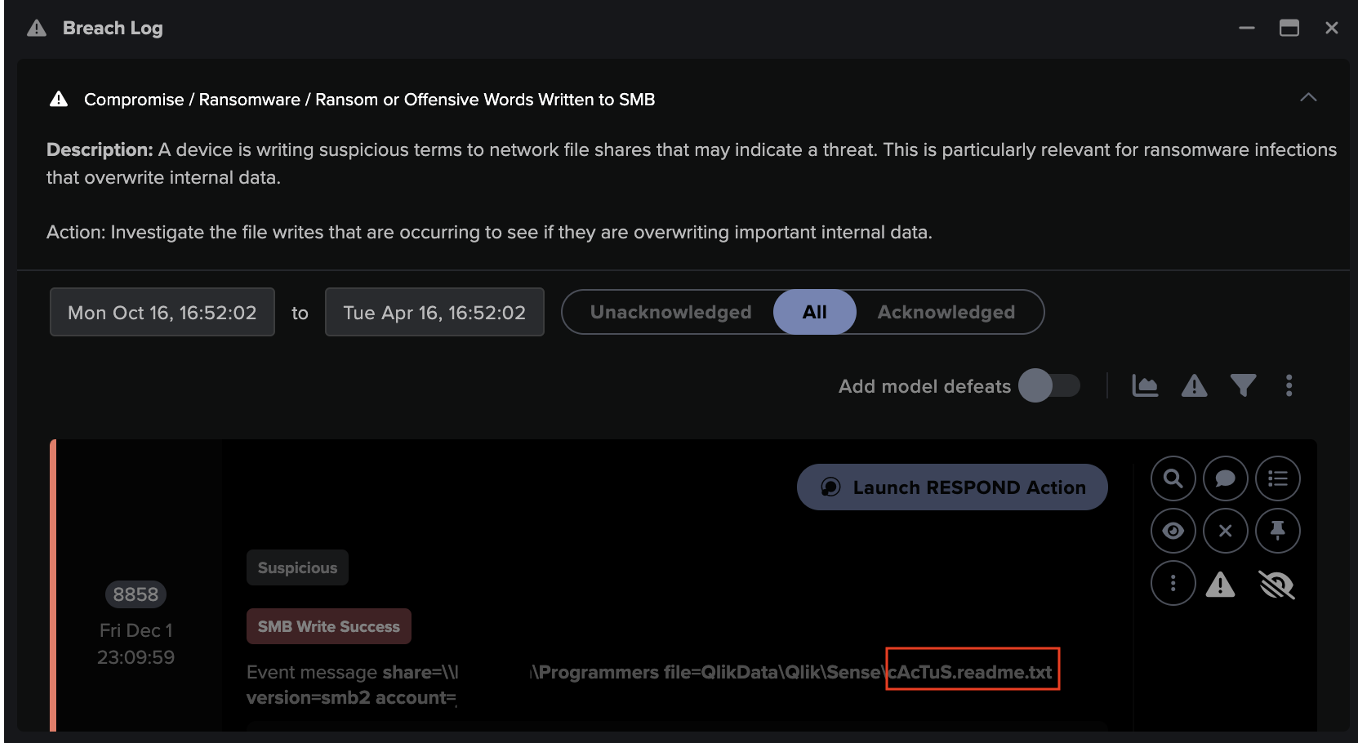
Triggered by this unusual activity, Darktrace’s Cyber AI Analyst launched an investigation into all observable stages of the kill chain including command and control connections, suspicious executable SMB writes and privilege escalation.
It then automatically generated an incident summary showcasing every stage of the attack, surfacing all the information the security team needed for a fast response.
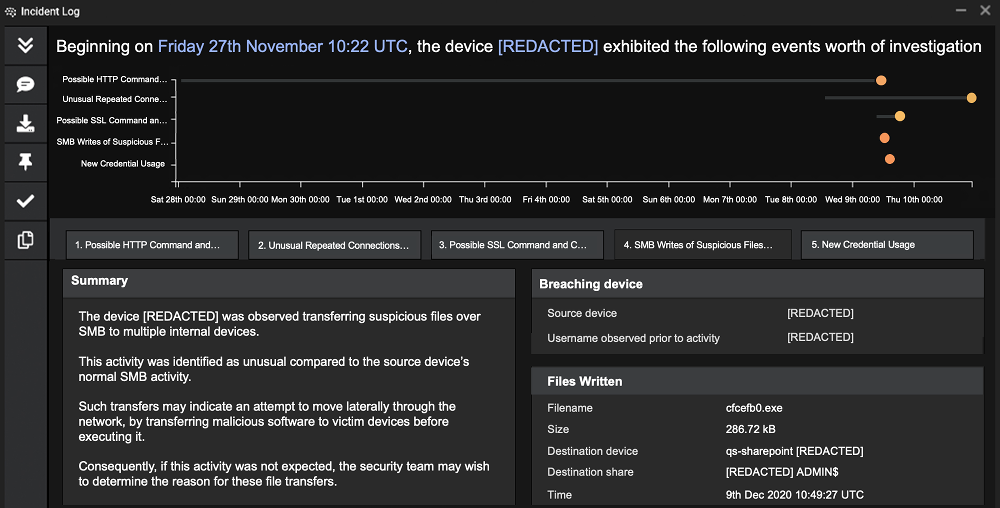
Figure 2: Cyber AI Analyst triaged and reported on the malicious activity from the device, surfacing useful metrics and natural language summaries for each stage of the kill chain.

Figure 3: This graph from the Darktrace UI displays how Cyber AI Analyst detected the various stages of the kill chain and correlated the timeline of events.

Figure 4: Darktrace reveals the spike in external connections in blue for the device and the DCE-RPC requests in green. The dots represent model breaches triggered by the unusual suspicious activity originating from the device. The external connection spikes match the internal DC-RPC request spikes indicating the device is attempting to move laterally during the C2 connections.
In this case, real-time detections from Darktrace’s AI coupled with a high-confidence alert from Darktrace’s SOC team enabled the company’s security team to isolate the device from the network, successfully containing the attack before encryption began.
While having AI-powered detection was enough to stop the attack in this scenario, relying on detection alone is playing with fire. With the average dwell time of attacks shrinking – particularly in the case of ransomware – Autonomous Response is becoming critical in taking action on behalf of human teams. Attackers are increasingly striking out of hours, when these teams aren’t available to respond, and performing exfiltration and encryption rapidly. In these cases, detection without immediate response is futile.
Autonomous Response: Revolutionizing ransomware defense
Recent galvanizing attacks have propelled us into a new era of ransomware. 65% of C-suite and other executives say that ransomware will be a major issue they face over the next twelve months.
An over-reliance on security defenses that depend on rules, signatures, and historical data has proven to leave organizations vulnerable to novel ransomware. Failure to prepare for the unknown often forces businesses into a difficult dilemma when it comes to ransomware: either pull the plug to stop the encryption by taking everything offline, or face encrypted systems, and be confronted with a hefty ransom.
But there is a third way, one which uses Self-Learning AI to understand your organization from the ground up to spot subtle deviations indicative of a cyber-threat, regardless of whether it has been seen before. Moreover, Autonomous Response ensures that fast, precise action will be taken against attacks whenever they occur. While even the most attentive human teams cannot hope to match the machine speed of modern ransomware attacks, Autonomous Response halts these sophisticated threats the moment they emerge. It really is the only way to truly level the playing field against today’s ransomware attacks.
Thanks to Darktrace analyst Dylan Evans for his insights on the above threat find.
Darktrace model breaches:
- Anomalous Connection / Anomalous SSL without SNI to New External
- Anomalous Connection / Posting HTTP to IP Without Hostname
- Experimental / Possible Emotet Callback URL
- Device / Large Number of Model Breaches
- Device / Lateral Movement and C2 Activity
- Compromise / SSL or HTTP Beacon
- Device / Multiple Lateral Movement Model Breaches
- Compromise / Suspicious SSL Activity
- Compromise / Unusual SMB Session and DRS
- Compromise / Suspicious Spam Activity
- Compromise / Unusual DRS Activity
- Anomalous Connection / High Volume of New or Uncommon Service Control
- Compromise / Beaconing Activity To External Rare
- Compliance / SMB Drive Write
- Experimental / Anomalous GetNCChanges and Kerberos Ticket
- Experimental / New or Uncommon SMB Named Pipe V4
- Device / Large Number of Connections to New Endpoints
- Anomalous Connection / New or Uncommon Service Control
- User / New Admin Credentials on Client
- Anomalous Connection / Possible Outbound Spam
- Compromise / New or Repeated to Unusual SSL Port
- Compromise / Slow Beaconing Activity To External Rare
- Anomalous Connection / Anomalous SSL without SNI to New External
- Experimental / New or Uncommon SMB Named Pipe V3
- Experimental / Anomalous DRSGetNCChanges Operation
- Anomalous Connection / Possible Callback URL
- Compromise / Sustained SSL or HTTP Increase
- Anomalous Connection / Multiple SMB Admin Session
- Anomalous Connection / Rare External SSL Self-Signed
- Anomalous Connection / Posting HTTP to IP Without Hostname
- Device / New Failed External Connections
- Anomalous Connection / Suspicious Self-Signed SSL
- Compromise / SSL Beaconing to Rare Destination
- Compromise / HTTP Beaconing to Rare Destination
- Experimental / Rare Device TLS Agent
































![Cyber AI Analyst Incident Log showing the offending device making over 1,000 connections to the suspicious hostname “zohoservice[.]net” over port 8383, within a specific period.](https://assets-global.website-files.com/626ff4d25aca2edf4325ff97/662971c1cf09890fd46729a1_Screenshot%202024-04-24%20at%201.55.10%20PM.png)